Today we will learn how to perform Penetration testing of Man-In-The-Middle (MITM) attack using ARP Spoofing. At first we must understand what is ARP spoofing and how hackers can use it to exploit and execute severe MITM attacks.
Penetration testing of Men in Middle Attacks using ARP Spoofing
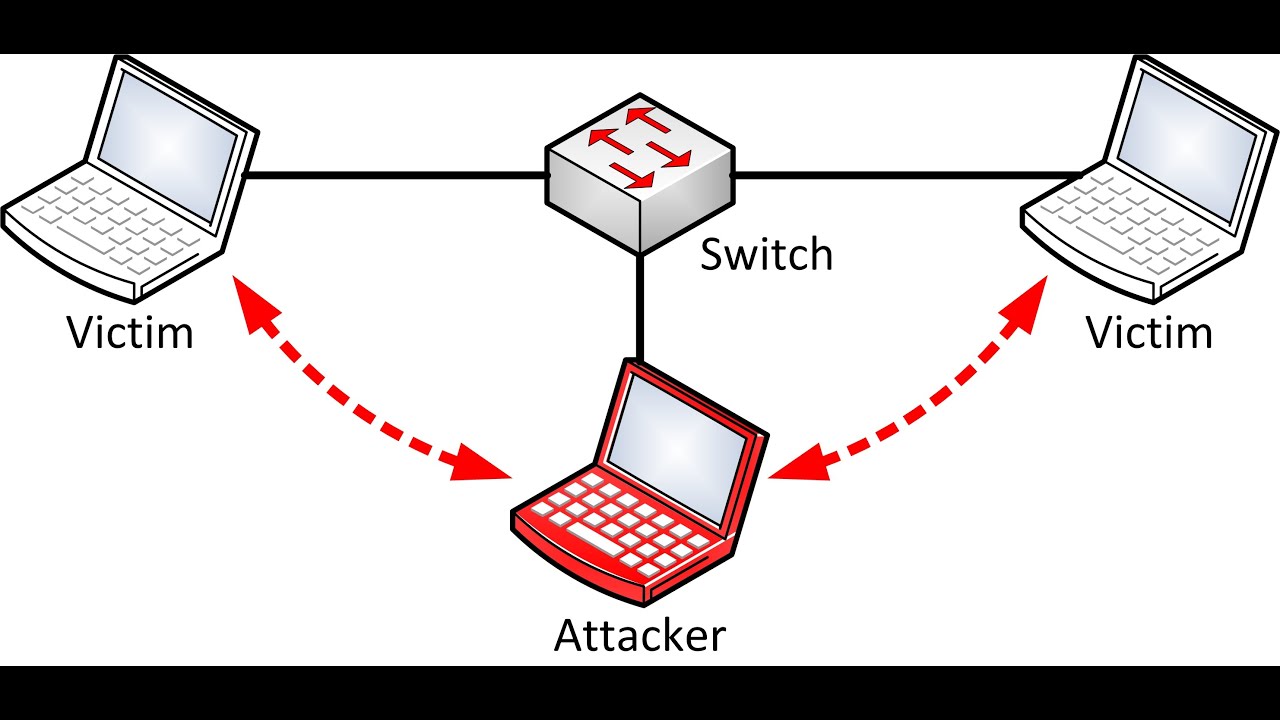
ARP spoofing is a type of attack in which a malicious actor sends falsified ARP (Address Resolution Protocol) messages over a local area network. This results in the linking of an attacker’s MAC address with the IP address of a legitimate computer or server on the network. Let’s see how to Pen test Man-In-The-Middle Attack by ARP spoofing of machine. So letz get started..
Requirements:
1).Kali Linux
2).Victim
3).Tools that are preinstalled on kali
Pen testing of Men in middle attacks using ARP spoofing
Step 1:
In this step we will scan the network for a victim’s computer which is alive using the most powerful scanner NMAP.
Here is the command to scan:
nmap –F 192.168.0.100/24
Here my victims ip is 192.168.0.108
Step 2:
Now lets setup a ip forwarding in the kali machine to enable victim to surf the web when he is attacked..
Command:
echo 1 > /proc/sys/net/ipv4/ip_forward
Step 3:
Now lets arpsoof our victim whoes ip address is 192.168.0.108 using the following commands..
Command 1:
arpspoof –i eth0 192.168.0.108 192.168.0.1
[here 192.168.0.1 is my default gateway & eth0 is my Ethernet device]
Command 2:
arpspoof –i eth0 192.168.0.1 192.168.0.108
Step 4:
Now to test whether if man-in-the-middle attack is successful we use the tool that are pre-installed in kali..which are Driftnet and Urlsnarf
Open up a window and type driftnet –i eth0 which opens up a small window that captures all the graphics that the victim surf on the web.
Keeping up the above window open, Open up another window and type urlsnarf –i eth0. Urlsnarf gives the details of the URL’s that the victim browse on the web.
Below is the screenshot of the successful MITM attack using ARP Spoofing.
That’s it, hope u liked this tutorial!! I will be coming up with much more tutorial.
Thank you!!





No comments:
Post a Comment